How Identity Cloaker Works
The intention of this page is to briefly illustrate the main potential threats
of the nowadays Internet in the most common situations and how Identity Cloaker
helps to minimize them. It is absolutely in no way a comprehensive description
of all the potential benefits you get when using Identity Cloaker. And without
even distantly trying to insult you, you should keep this motto in mind:
"If you believe Internet is a safe place, you simply don't know enough!"
- Situation 1: Direct Internet connection at home,
without Identity Cloaker
- Situation 2: Direct Internet connection at home,
with Identity Cloaker
- Situation 3: Connected from company/university
etc., without Identity Cloaker
- Situation 4: Connected from company/university
etc., with Identity Cloaker
Situation 1: Direct Internet
connection at home, without Identity Cloaker

Main potential threats:
- ISP activity logging (L) - in some countries and specific situations
- Data sniffing by hackers (H)
Description: While under normal circumstances the threat of the Internet
Service Provider doing something evil is relatively low unless you live in a
country which loves to spy their own citizens (well, there are quite a few of
such countries...), you are an easy prey for any devilish hacker - mainly if
you are connected to the Internet through wireless connection (such as WIFI).
Back to Top
Situation 2: Direct Internet
connection at home, with Identity Cloaker

Description: On this picture you can see how Identity Cloaker protects you
in a situation when you are connected to the Internet at home without any "internal
proxy server" usually required when connected from a company or university (for
example).
Using the Identity Cloaker client application, you create an encrypted secure
tunnel from your PC to one of the proxy servers provided by Identity Cloaker,
which then acts as the "middleman" between your PC and the destination server.
Since the data sent between you and the Identity Cloaker proxy server is encrypted
with a 256-bit impenetrable cipher, neither your Internet Service Provider,
nor any potential hacker or unwelcome guest can see the transferred data.
All they can see is nothing but "gibberish". We use an extremely strong
Rjindael AES-256 cipher to protect your transmitted data. This cipher is
considered "military class" and is currently one of the best and strongest ciphers
available in the world. Please note that the use of such a strong cipher may
be unlawful in some countries.
Back to Top
Situation 3: Connected from
company/university etc., without Identity Cloaker
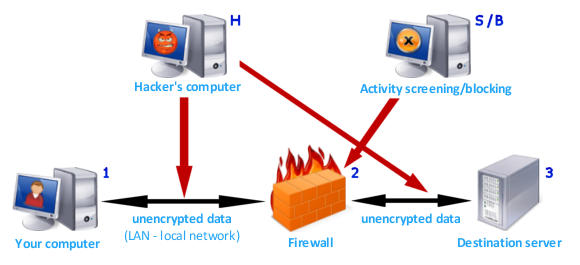
Main potential threats:
- Company / university / Internet cafe Internet activity screening and
blocking (S / B)
- Data sniffing by hackers (H)
Description: A very common situation when you are connected to the Internet
from your company, university, Internet cafe etc. The data sniffing (by hackers)
can take place at two parts of the data transmission path. Between your computer
and the company firewall, and between the company firewall and the destination
server - or actually between the company firewall and the Internet Service Provider.
The potential threat of data sniffing by the hacker in the first case (between
your PC and the company firewall) is relatively low because unless the Local
Area Network is using wireless connections such as WIFI, the hacker would have
to gain physical access to the local network (possible but usually complicated),
in the second case (i.e. between the company firewall and the ISP) the threat
of data sniffing is more likely to take place and is quite high.
Also, it is a common practice in the company / university, Internet cafe
environment to have the firewall set to block some websites and report all attempts
to visit such websites to the network / firewall administrator.
Back to Top
Situation 4: Connected from
company/university etc., with Identity Cloaker

Description: On this picture you can see how Identity Cloaker protects you
in a situation when you are connected to the Internet from your company, university
or Internet cafe and have to connect to the Internet through "internal proxy
server" / firewall.
Using the Identity Cloaker client application, you create an encrypted secure
tunnel from your PC to one of the proxy servers provided by Identity Cloaker,
right through the firewall, which then acts as the "middleman" between your
PC and the destination server. Since the data sent between you and the Identity
Cloaker proxy server is encrypted with a 256-bit impenetrable cipher, neither
your network / firewall administrator, nor any potential hacker or unwelcome
guest can see the transferred data.
All they can see is nothing but "gibberish". We use the extremely strong
Rjindael AES-256 cipher to protect your transmitted data. This cipher is
considered "military class" and is currently one of the best and strongest ciphers
available in the world. Please note that the use of such a strong cipher may
be unlawful in some countries.
The technique described on this picture is sometimes colloquially referred
to as "punching holes in firewalls". It's an extremely powerful technique that
allows you to override any web browsing restrictions set on the firewall level
by the firewall admin. Once the secure tunnel is established between your PC
and one of the Identity Cloaker proxy servers (through the firewall), you gain
the same web access rights as the proxy server itself. Since the proxy server
can access any website, so can you...and without anyone knowing!
Please understand that we do not say it's a good idea to breach any rules
set by the firewall administrator. You and only you will be responsible for
doing so. To be honest, we don't care about your company / university rules.
We care about laws. Naturally, you can't use Identity Cloaker for doing anything
unlawful. Please see the
Frequently Asked Questions which explains this topic further.
Back to Top
Has this page failed to answer your questions? Please check our
Frequently Asked Questions or contact our
customer support.

